
Building AI Agents: The Architecture Guide We Wish We Had
Building AI Agents: The Architecture Guide We Wish We Had Building AI agents turned out to be one of those adventures that started with wide-eyed

GDPR stands for the General Data Protection Regulation. The GDPR is a set of rules and regulations that were implemented on 25-May-2018. These regulations are applied to any organisation inside or outside of the EU that stores or processes any data belonging to EU citizens.
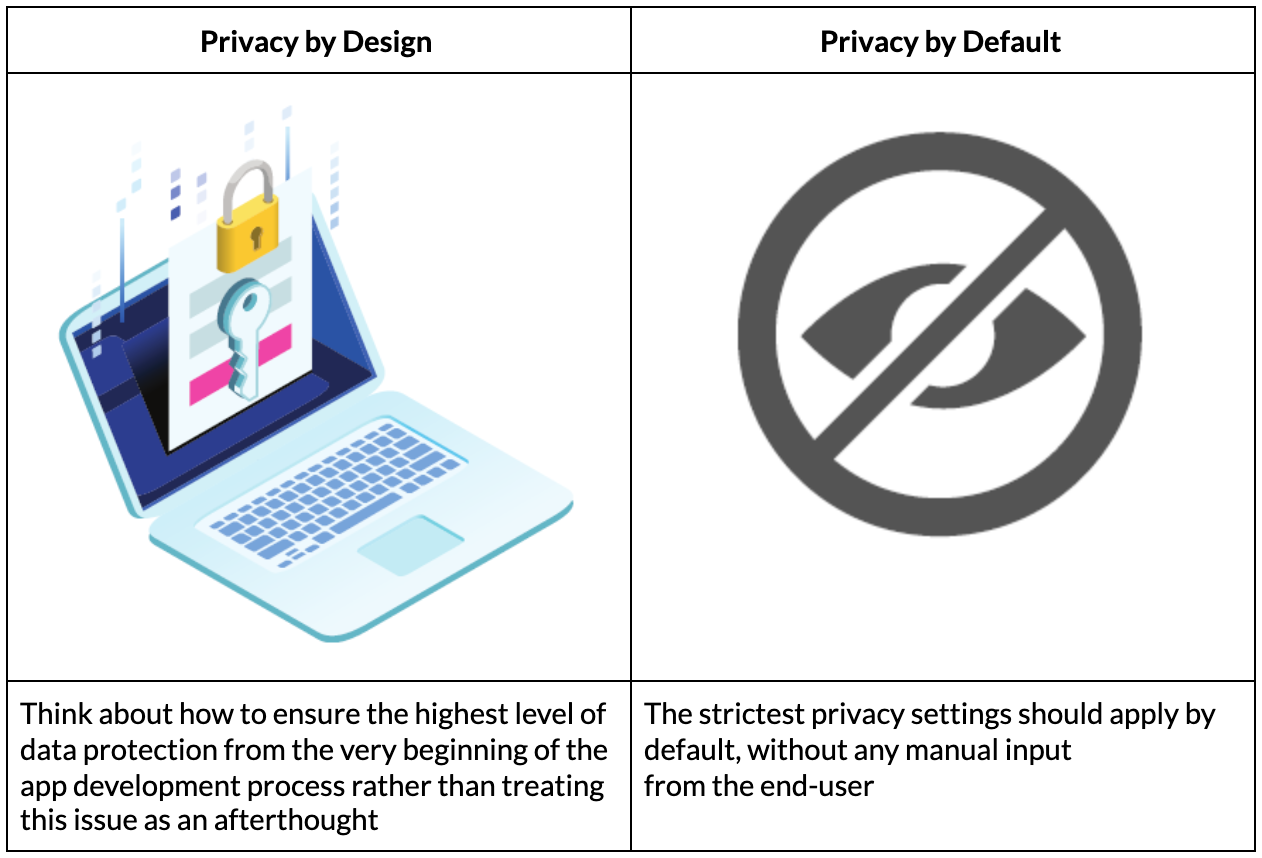










Under GDPR, companies processing certain kinds of data must appoint a Data Protection Officer (DPO), a named individual who is accountable and responsible by law for an organization’s privacy compliance, including PbD. This requirement is regardless of a company’s size, which means that even the tiniest business engaged in certain kinds of data processing must appoint a DPO.
It is encouraged to voluntarily appoint a DPO regardless of the nature of their work. DPO acts as the health and safety officer for privacy. DPO acts as the “good cop” to keep the development processes legally compliant and acts as the “bad cop” if the practices slip.
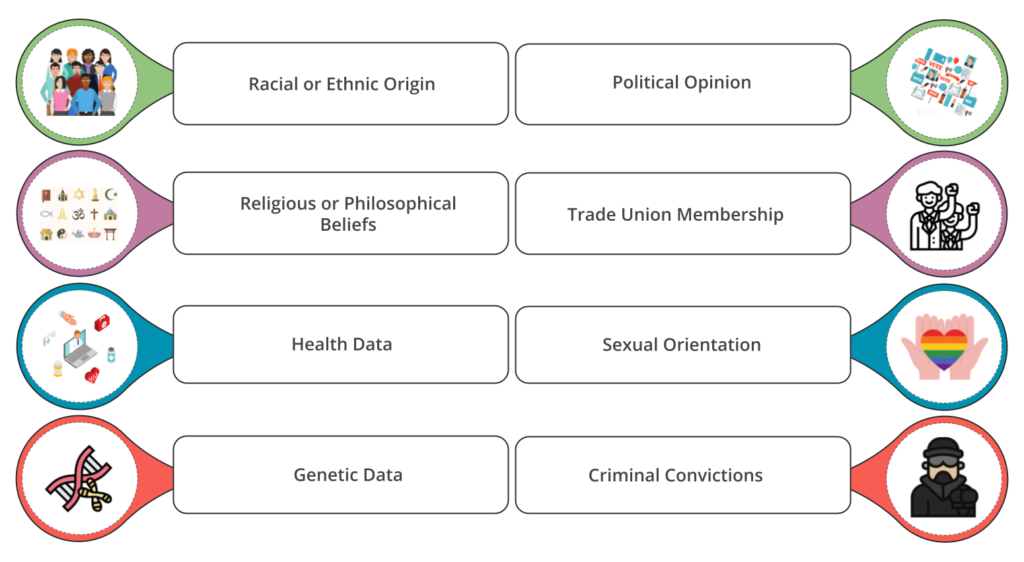






Identify the source and type of information gathered. Who collected the information, the method and for what purpose?
How and when will the information be used?
Does the person have authorization?
How will authorized users be identified?

How and when will the information be used?
Does the person have authorization?
How will authorized users be identified?















Example: Granular permissions – Facebook
Users can choose which permissions they grant through a permission request flow. For example, if an app requests “Page and Groups” permission, people receive a request to grant those permissions.


Example: List of 3rd Parties – Paypal
PayPal’s notice lists over 600 third-party service providers – https://www.paypal.com/uk/webapps/mpp/ua/third-parties-list

Contact us to find out how Techpearl can develop the best apps according to your requirements adhering to the General Data Protection Regulations.

Building AI Agents: The Architecture Guide We Wish We Had Building AI agents turned out to be one of those adventures that started with wide-eyed

Angular Best Practices for Scalable and High-Performance Applications Introduction Staying current with Angular’s latest features is key to writing efficient, scalable, and maintainable applications. This

Breaking the API Mold: A new era of AI-Driven Customer Journeys In the fast- paced world of financial services, speed, accuracy and scalability are critical.
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checkbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checkbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |