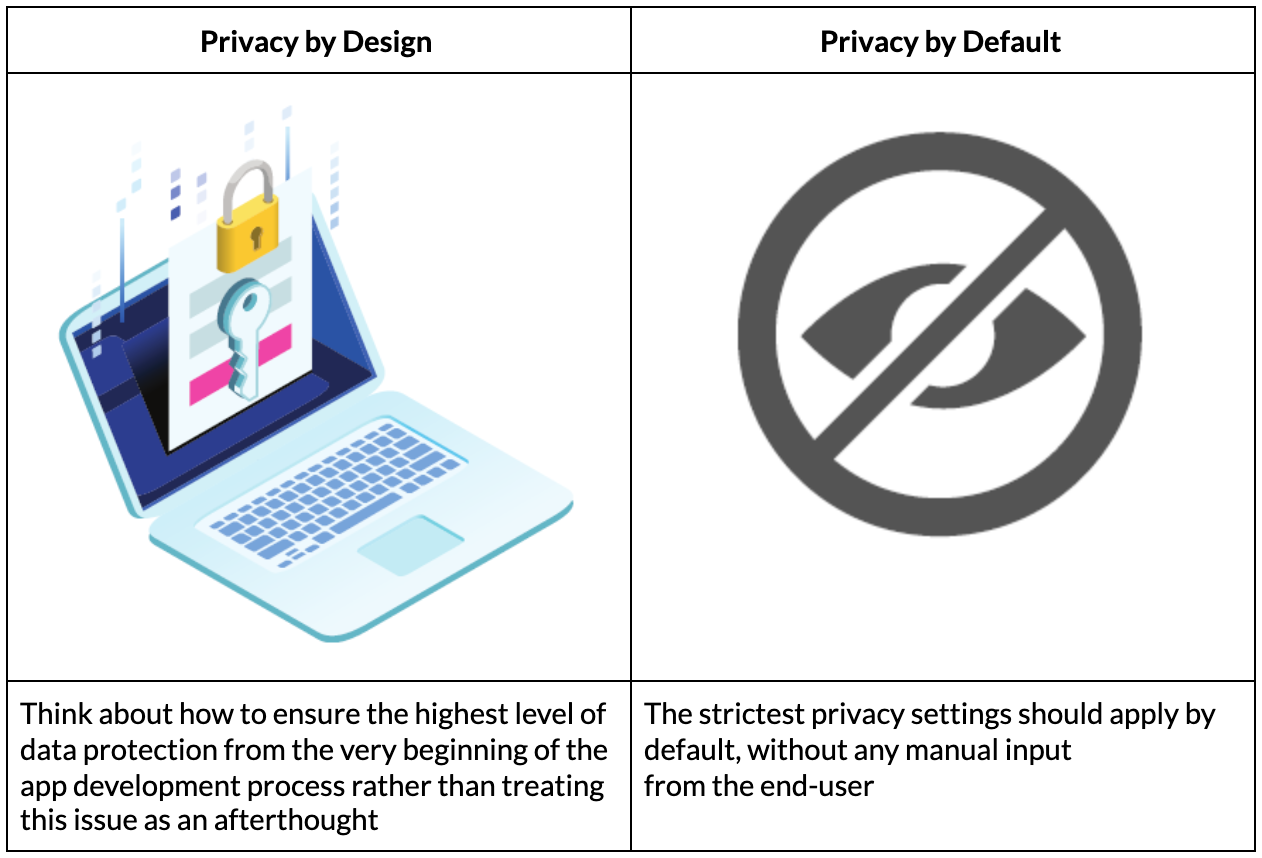
Creating PDF and Converting to PDF/A using Python and Ghostscript
Creating PDFs programmatically is a common need in modern applications, whether for reports, invoices, certificates, or other documents. However, when systems require long-term archiving, regular